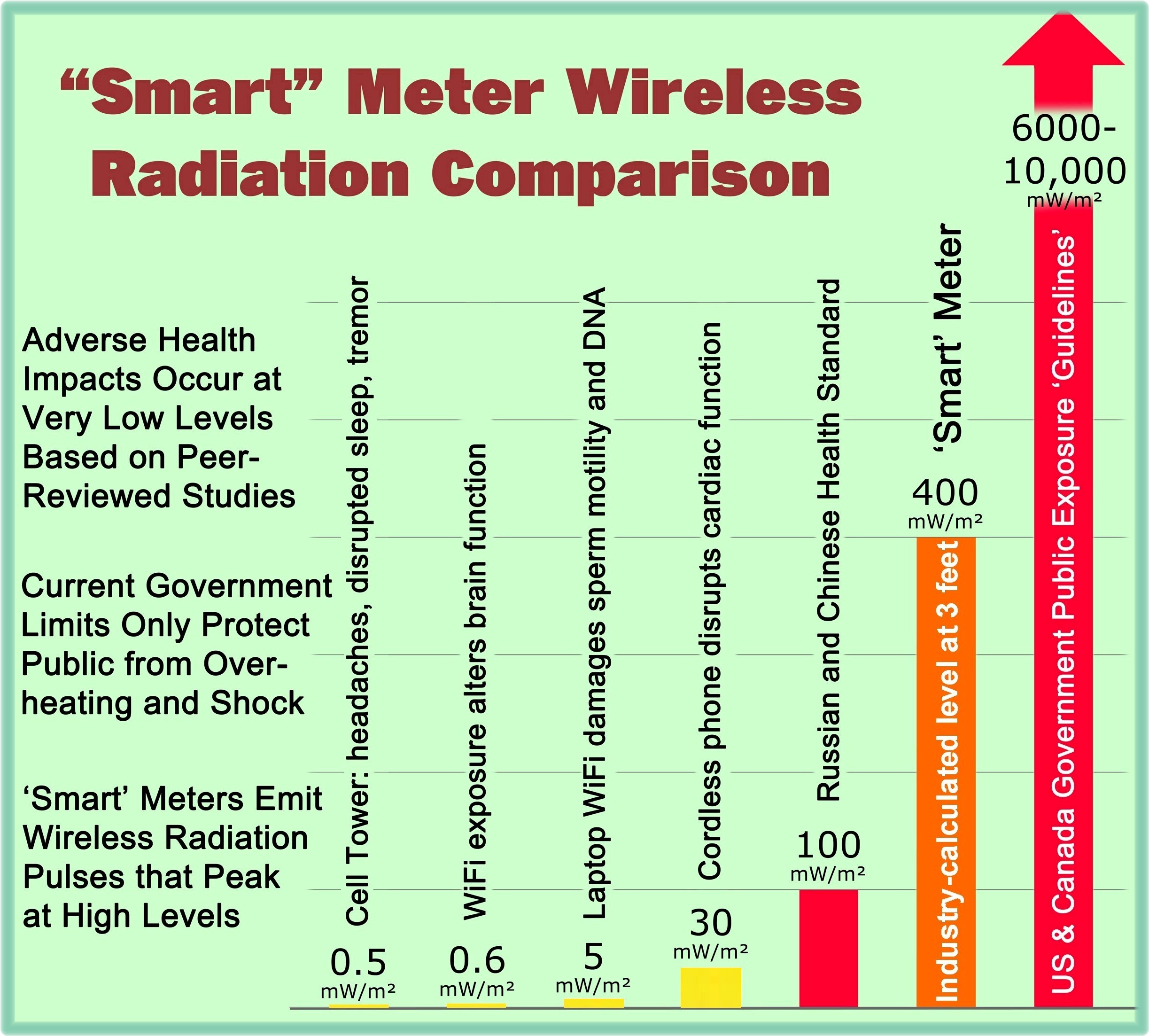
by K.T. Weaver, SkyVision Solutions
 Within the last few months, there have been Congressional testimonies by expert witnesses further revealing that utility ‘smart’ meters increase the vulnerability of our electric grid to cyber attacks. These testimonies do not generally make it into the daily news broadcasts or newspapers that would help raise public awareness of the threats, but articles written for this website include:
Within the last few months, there have been Congressional testimonies by expert witnesses further revealing that utility ‘smart’ meters increase the vulnerability of our electric grid to cyber attacks. These testimonies do not generally make it into the daily news broadcasts or newspapers that would help raise public awareness of the threats, but articles written for this website include:
Consistent with the Congressional testimonies, I found a peer-reviewed paper published earlier this year that provides substantiating evidence for cyber threats posed by utility smart meters. The paper is entitled, “Resiliency of Smart Power Meters to Common Security Attacks.” Unfortunately, the title of the study is misleading since its content actually concludes that current smart meter technology is not resilient to common security threats.
As I have done for other topic areas, I will present carefully selected excerpts from the published paper to help raise public awareness of the threats posed by smart meters and the smart grid. This information is intended to counterbalance the propaganda disseminated by the smart grid industry that “everything is fine.”
In selectively quoting the published study, I will occasionally provide emphasis with bold font.
Abstract for the Published Study, “Resiliency of Smart Power Meters to Common Security Attacks.”
“The development of Smart Grid power systems is gaining momentum in many countries leading to massive deployment of smart meters to realize the envisioned benefits. However, there are several concerns among the consumer communities and the service providers with respect to information security when it comes to the deployment of smart meters. This paper attempts to address the main challenge related to smart grid information security by examining the resiliency of smart meters to security threats and attacks. Several common information security attacks are being used to study their impact on the performance of smart meters in a controlled laboratory environment. Results obtained showed drastic effect on the functionality of smart meters and their associated data gathering servers.”
Quoting from the Study “Introduction”
“One main component of a Smart Grid deployment is the Advanced Metering Infrastructure (AMI) using smart meters at the consumers’ premises and substations. … The essential functions of a typical smart meter includes: recording real-time electricity usage; transmitting this [granular data] to the smart grid; and receiving communications from the smart grid. Additional features of the smart meter include tracking data usage to identify patterns and behaviors; the ability to disconnect the customer from the power grid; alert utility company when problems occur; interface with smart appliances in a home to control their operation during peak times; and to support on-site renewable energy generation and exporting this energy to the grid via net-metering agreement.”
“However, with the deployment of smart meters, comes a major concern of information security related to consumers’ privacy, data integrity, authentication, access control, system availability and several others. This is because smart meters are considered the weakest link when it comes to possible security breaches. This is the case, as smart meters are easier to be attacked through associated home and neighborhood networks especially when these networks rely on wireless communication technologies.”
“In this work we examine how common security attacks such as the Denial of Service (DoS) attack and the Man-in-the-Middle attack (MiM) can be exploited against smart power meters within a Local Area Network (LAN). The results shown in this paper present the negative effect such attacks can have when generated. Although these attacks are being generated within an isolated laboratory environment, generalization of such attacks to be managed remotely by hackers is possible causing the same effect.”
“Common Security Attacks” Outlined in Study
DoS Attack
“A DoS attack when launched against any system or component its main objective is to cripple the system ability to function as intended. Thus denying legitimate users of such a system expected services. This is usually accomplished by launching an attack to overload the system beyond its capabilities.”
Man-in-the-Middle (MiM) attack
“MiM is one of the most common attacks which can be used as an active or passive attack. In its most obvious forms, a MiM attacker uses a tool to intercept network traffic between two communicating parties, for example, a smart meter and it associated server. The attacker then can perform a range of malicious actions depending on its intensions.”
“In this work we focus on performing a MIM sniffing attack to re-route exchanged network traffic between two target hosts to a malicious host which will forward to the original intended destination without any noticeable delay. This will make it difficult for the target hosts to notice that their traffic is being sniffed by a malicious attacker. This is performed in a switched LAN environment by corrupting the [Address Resolution Protocol] ARP cache entries of the target hosts using an ARP cache poisoning mechanism.” Note: “Hosts with corrupted ARP cache entries are usually unable to communicate properly with the other network hosts…”
Lack of Robustness of Power Smart Meters against DoS Attacks as Outlined in the Study
“In this experiment, we investigated the effect of the aforementioned common DoS attacks on the performance of two types of smart meters, namely Power Quality Meter SHARK 200 Meter and Power Nexus 1500 Meter. The experiment was performed by launching the DoS attacks on the smart meters, and then studying their robustness against such attacks, …”
Important Note
The authors of the published paper make their conclusions regarding utility smart meters based upon testing performed on meters not normally used for residential purposes. For example, the Nexus 1500 meter is marketed as the “most advanced monitoring product on the market today” for applications such as highly critical industrials, hospital/medical, and utility transmission line substations. The Shark 200 meter would most likely be used for commercial and industrial applications as well as monitoring for utility substations. The meters are manufactured by Electro Industries/Gauge Tech, “The Leader in Power Monitoring and Smart Grid Solutions.”
Results from DoS Attacks
“The results of conducted experiments demonstrated clearly that DoS attacks had a significant negative effect on the smart meters’ performance. … when the rate of a DoS attack traffic increases considerably, smart meters may crash and disconnect from the network. This demonstrates clearly that the tested smart meters are vulnerable to common DoS attacks, and have no security protection mechanism to countermeasure against such attacks.”
Lack of Robustness of Power Smart Meters against ARP Cache Poisoning Attacks as Outlined in the Study
“In this attack scenario, the attacker host attempts to corrupt both the ARP caches of the target smart meter and its associated server, using the APR cache poisoning technique. The objective of this attack is to reroute the network traffic exchanged between the smart meter and the smart server to a non-legitimate destination, which is the attacker host. Once the rerouted traffic is sniffed by the attacker host, it is then forwarded to the legitimate destination. To perform this kind of MiM attack, the attacker host needs to enable its IP routing feature. Then, the attacker host proceeds to corrupt the ARP caches of the smart meter and server by sending fake ARP requests, as shown in the Fig. 5.”
“The results of this experiment demonstrate clearly that the attacker host succeeded to reroute the traffic exchanged between the smart meter and the server, using the ARP cache poisoning attack. … Overall, all the conducted experiments show clearly that the tested two smart meters and associated servers running associated smart grid application software are vulnerable to common DoS attacks as well as to the ARP cache poisoning attacks. Hence, the tested smart meters and associated servers can be easy targets of common network attacks which might compromise secure communication for exchanged smart grid data.”
Study Results: Smart Meters Are Easy Targets within the Grid
“The security analysis conducted in this paper shows that the tested smart meters have been designed without security consideration to countermeasure against the two main common security attacks, namely the DoS and the ARP cache poisoning attacks. Hence, smart meters can be easy targets of malicious network traffic and users. Usually, smart meters are designed to offer ease to use and practical user interfaces with an effective cost model in mind. However, our work in this paper shows that the tested smart power meters lack basic security functions, such as packet filtering capabilities and integrated Intrusion Detection/ Prevention functionalities to detect and prevent possible malicious attacks or simple passive monitoring attacks. Consequently, their availability and efficiency may become questionable within an implementation of a secure smart grid network.”
Despite the warnings contained in the Congressional testimonies mentioned at the beginning of this article, the published study highlighted here, and the many other articles written on smart meter cyber security threats as well as other significant risks to consumers and society posed by smart meters, massive meter deployments continue. Last year I wrote an article entitled, When Will the Smart Meter Insanity End? That question remains unanswered.
Related Articles on Cyber Threats for Smart Meters
Other articles posted at this website posted during the course of 2015 revealing the cyber threats posed by smart meters include the following:
- From India: Smart Meter Cyber Attacks ‘Could Bring the Country Down to its Knees’
- Smart Meters ‘Wide Open’ to Cyber Attacks That Can Cause ‘Havoc’ Says Hacking Expert
- “The consequences of deploying bad stuff [smart meters] are dire.”
- Smart Meters Put Grid Security at Risk
- U.S. Power Grid Being Hit With ‘Increasing’ Hacking Attacks as Smart Meter Deployments Continue
- Smart Meters Are Not Secured
Primary Source Material for this Article
“Resiliency of Smart Power Meters to Common Security Attacks,” by Khaled Shuaiba, et.al; Procedia Computer Science 52 (2015) 145 – 152; presented at the 6th International Conference on Ambient Systems, Networks and Technologies (ANT 2015), available at http://www.sciencedirect.com/science/article/pii/S1877050915008492





Apart from books cyber-security issues are presumed as theoretical unless these threats are demonstrated it will still be regarded as such.
Pingback: Tshwane Mayor dismisses allegation that his Municipality misspent R4 billion » News101
Pingback: Smart Meters: ‘Easy Targets’ for Hackers and ‘Malicious Network Traffic’ within the Electric Grid, Reveals Latest Research Study | Stop "Smart" Meters, Florida!
So what? Who would waste time hacking a smart meter? The worse I see that could happen is they shut off your electricity. But I’ve never heard of that happening. There is no tie between smart meters and the electric grid or any power generation network. Hacking a smart meter could not get you access to either. Maybe you should be more concerned about posting private information on an open network such as Facebook or allowing Google to remember your every search and sites visited.
I sense you didn’t actually read the article or embedded links. As stated in recent GAO Congressional testimony:
“[C]ybersecurity experts have demonstrated that certain smart meters can be successfully attacked, possibly resulting in disruption to the electricity grid.”
Plus, smart meters ARE part of the “electric grid.”
Utilities have typically relied upon an “air gap” separation between grid systems and the Internet. Now a simple “thumb drive” can bridge that gap or otherwise hacking into wireless networks.
I AM concerned about private information and thus do not have a personal Facebook account, and I don’t use Google as my search engine, plus a number of other precautions that I take. [This website maintains a Facebook page but only contains links to articles at this website.]