by K.T. Weaver, SkyVision Solutions
This past week there was a meeting of BlackHat USA 2015 in Las Vegas, where InfoSec professionals met. As part of a blog article written about this meeting, there was the following updated entry by Steve Ragan who attended the meeting:
 “I had an interesting discussion after getting my badge at DEF CON this afternoon about smart grids.
“I had an interesting discussion after getting my badge at DEF CON this afternoon about smart grids.
A friend of mine reminded me of a talk given during BSides Las Vegas last year about securing smart meter infrastructure. The focus of the talk was BC Hydro, the electric utility in British Columbia, and their move to smart meter adoption, as well as the security risks associated with this upgrade.
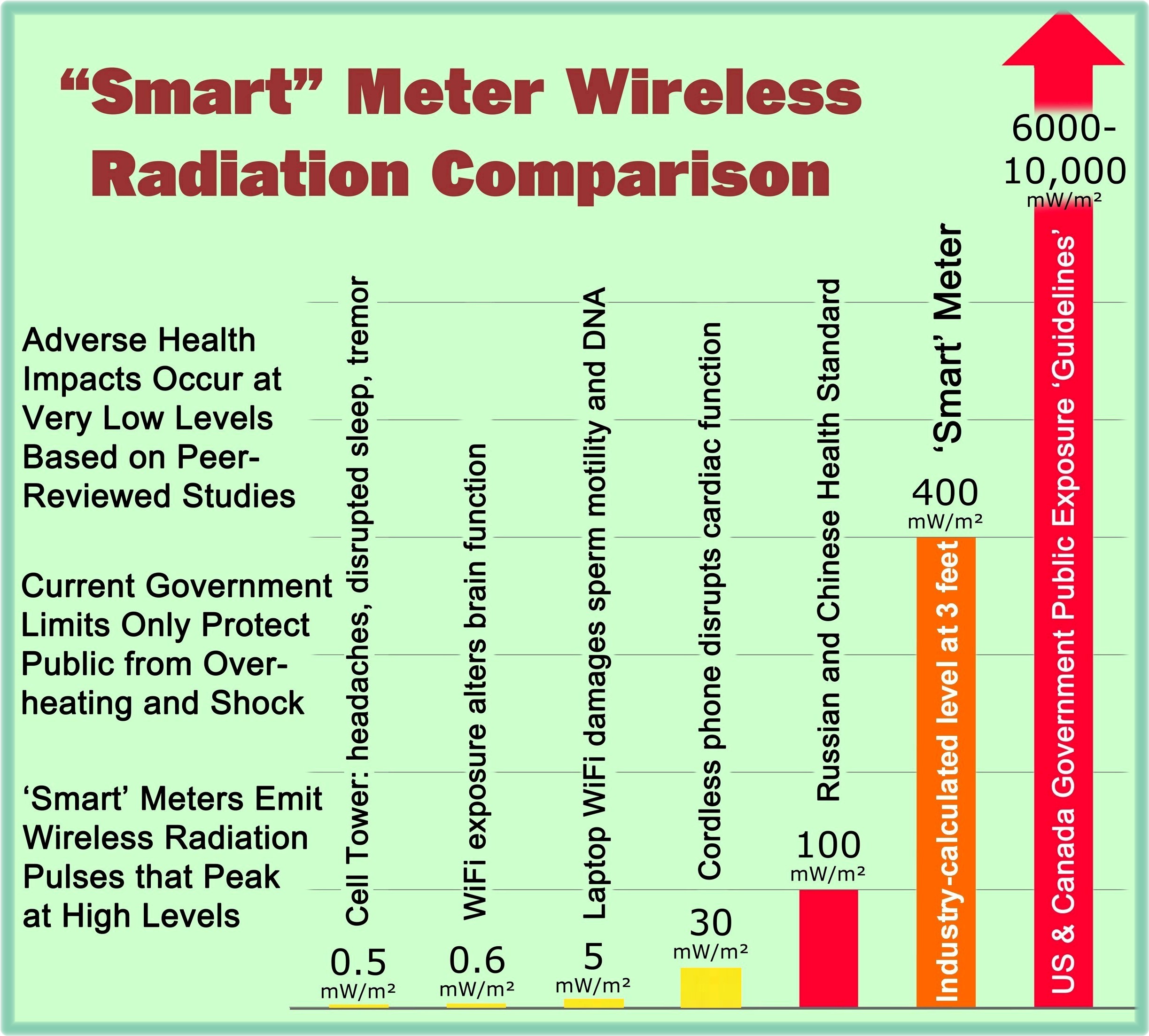
Smart meters and ICS [Industrial Control System] security issues are a serious topic in many parts of InfoSec due to their reach into a person’s home and life. It’s a talk worth watching,…”
Upon reading the above updated blog entry, SkyVision Solutions reviewed the video files for the BSides meeting from last year and discovered presentation materials and statements by presenters that were almost surreal in nature on the subject of smart meter vulnerabilities for what were called physical, cyber, and social threat vectors. The presentation from 2014 as described by the program information for the event was on the topic of “Security Testing for Smart Metering Infrastructure.”
Below are selected quotations from the presentation as well as an 8-minute video clip. I think you will find it quite revealing and instructional.
.
In the video, one presenter initially discussed four (4) different “Example AMI Hacks.” During that discussion, the following statements were made:
“A lot of the angst out there over AMI deployments is going to be over privacy issues. People have got a lot of concerns over what can I do with the data in a smart meter if the smart meter is co-opted versus a flywheel meter … which really had nothing that could be used by a bad guy.”

In discussing the threat vectors for smart meters, it was mentioned as to why people would want to attack smart meters:
“Well, the goals are at the bottom there: possibly turn off the power; mess with the billing, increase it, lower it, depending on what you want to do; know when people are home and what they’re doing.”
With all the risks and threats mentioned during the presentation, someone in the audience had the courage to ask:
“How serious would it have to be for us to halt deployment?”
The response, indicative of a mindset to move forward at all costs, was given as follows:
“In order to halt deployment there would have to be no other way to mitigate, change the use case, and so forth. … I can not imagine a situation where we would halt deployment, in other words, decide to put the flywheel meters back.”
The above response was given despite the fact that the presenter made the following additional commentary:
The consequences of deploying bad stuff are dire, and I don’t only mean because somebody’s going get the ability,… Most modern AMI deployments have remote disconnect and re-connect. OK. Bad guy can turn off the power if we don’t do our job right. So, the consequences are dire. … We really don’t want to deploy bad stuff. Not only for moral reasons, but if I deploy bad stuff, someone will know, they’ll probably know soon, and my chickens will home to roost.”
The presenter from BC Hydro acknowledged that the consequences from deploying smart meters can be dire, but yet he apparently rationalizes moving forward for what would have to be considered unknown reasons; there is just a mindset that they can’t imagine a situation where they would go back to what the presenter referred to as “flywheel meters.” Somehow, they just expect to avert disaster by staying one step ahead of the hackers even though it is a “crowded space” for both the “good guys” and “bad guys.”
Before closing, let me also state that there was a presentation at the BlackHat USA 2015 meeting this past week where it was reported that security researchers have exposed new flaws in ZigBee. ZigBee is one of the most popular wireless communication standards used by Internet of Things (IoT) devices and the almost exclusive protocol used for smart meters communicating with home appliances and smart meter-enabled devices.
Reportedly, ZigBee is inherently insecure making it possible to compromise ZigBee networks and take control of all connected devices on the network.
In conclusion, although smart meter deployments continue, there are more than ample reasons to halt deployments, with just some of the serious privacy and security threats outlined in this article. Utility executives, regulators, and others just need the courage to take the reasonable and prudent actions to avert disaster.
Source Material for this Article
“Black Hat 2015: Salted Hash live blog (Day 2),” at http://www.csoonline.com/article/2962314/security-awareness/black-hat-2015-salted-hash-live-blog-day-2.html
“Security Testing for Smart Metering Infrastructure,” at http://www.irongeek.com/i.php?page=videos/bsideslasvegas2014/bg11-security-testing-for-smart-metering-infrastructure-steve-vandenberg-robert-hawk
BSidesLV 2014 at https://archive.org/details/BSidesLV2014; videos were uploaded to the Community Forum at archive.org in August 2014 without the creation of a Creative Commons License. Credit for the general video presentation content is thus given to the Security BSides Las Vegas, Inc. and the event held in August 2014, entitled, “BSides LV 2014.”
“Oh no ZigBee, as another front opens on home networking insecurity,” at http://www.theregister.co.uk/2015/08/06/zigbee_insecurity_home_networking_oit/?page=1




For BC Hydro at least half of existing issues they are now aware of could be easily discarded from the very beginning would they use wired meters for their AMI just as they did in Ohio. There apparently was a corporate/government kick back biased closed door decision and Blitz Krieg deployment tactic to have installation finished before anyone educate yourself to the point to understand of how vulnerable wireless AMI is. Both BC Hydro and Ohio Power had coinciding the implementation timing. Both had the same market industry information. Yet big credit to Ohio Power they did know of wireless meters issue – all of them security, health, safety, etc, and they used full duty of care to openly admit it and go with wired solution. BC Hydro at the same time openly lied that they did not have wired option available at that time. Former BC premier Campbell had long lasting, and going far back relationship with Itron – the maker of meters chosen by BC Hydro. The government apparently had direct interest to keep going with less advanced, and insecure Itron equipment compared to available wired options.
The mere fact that meters in neighbourhood exchange their readings information relaying it to each other means that the meter on a particular house is sending the information from other meters not related to the home owner. The Utility in this case had to pay the owner a fee for co-location of their equipment which does their private commercial data relaying not related to the owner. They just ignored they violated the ownership rights at least. Wired meters have no such problem initially.
BC Hydro case is full of deception and bulling, and now they will add their security efforts burden to the tax payers while that could be way all different/cheaper/safer/ethical if they used their duty of care, yet they are monopoly submitting to no one, and listening no one. That is a pure form of the wildest unethical capitalism practice.
I am not familiar with a utility in the state of Ohio openly admitting to problems with wireless smart meters. Duke Energy, for example, has customers in Ohio and other states, and my information indicates Duke Energy Ohio does use PLC type smart meters (which have their own vulnerabilities). I would appreciate any information or links describing in more detail what you mean about “Ohio Power” having done its “full duty of care.”
Updated 8/26/15: Mark wrote me and indicated he meant “Idaho Power” rather then Ohio Power. The system installed is evidently a powerline-type system (TWACS) that does not use wireless signals to communicate through other people’s meters. I would say the system is certainly more secure from hacking but still has a number of drawbacks in comparison with traditional analog meters. Some people have also reported health problems with these systems although the documentation for this is much less than for wireless systems. Reportedly, the system cost much less money to install than for BC Hydro on a per meter basis.
Sounds like an a very risky way to deliver and bill for electric usage. When it does go down who will they pin the blame on? This is an opportunity for a “False Flag” event that would start another war or arrest a group of people.