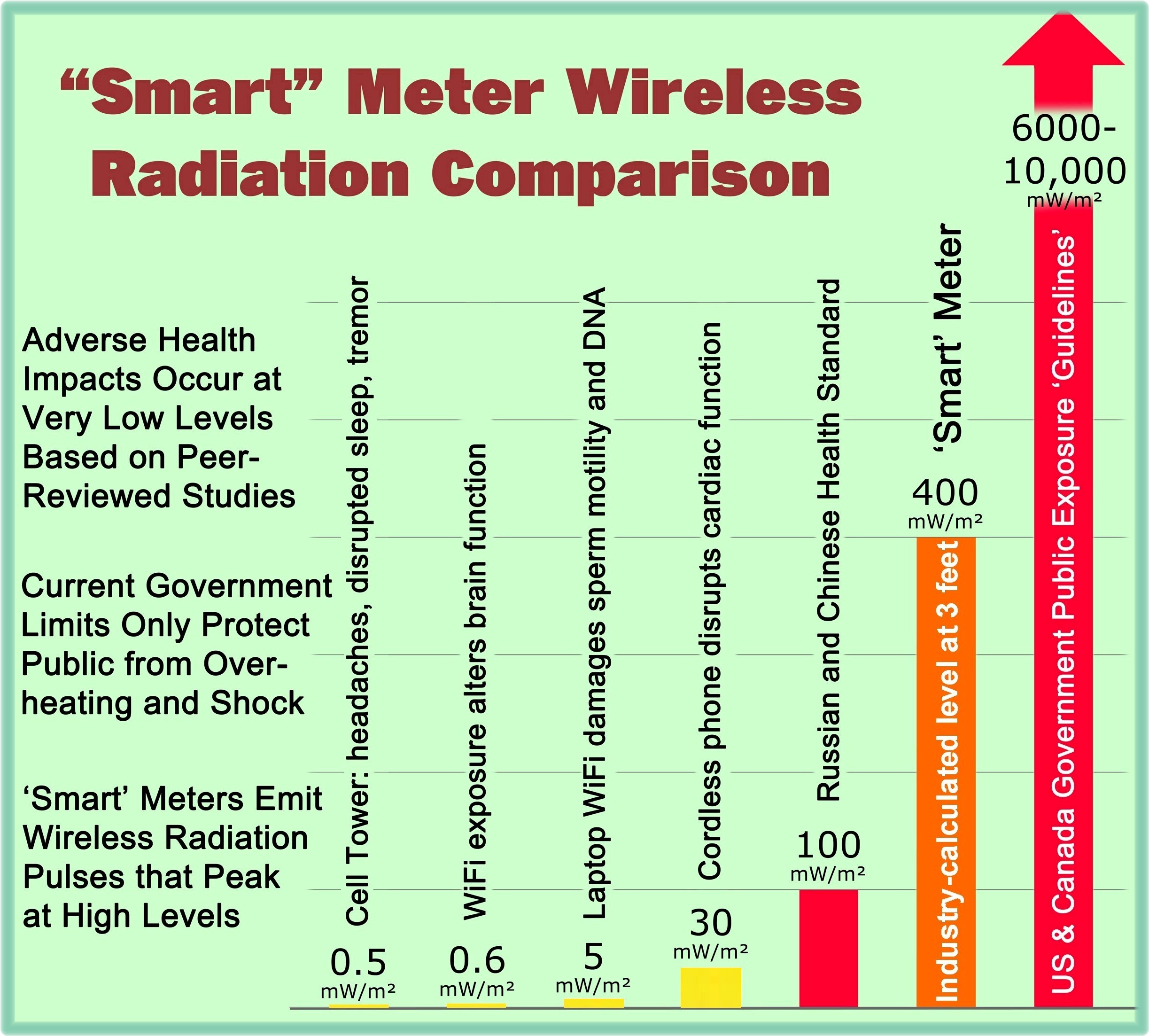
by K.T. Weaver, SkyVision Solutions
 The U.S. House of Representatives Committee on Science, Space and Technology Subcommittee on Oversight and the Subcommittee on Energy held a joint hearing titled Examining Vulnerabilities of America’s Power Supply on September 10, 2015. The purpose of the hearing was to “discuss various threats to the national electric grid, including: severe weather or other natural events; cyber, physical, or coordinated attacks; space weather; and electromagnetic pulse (EMP) attacks.”
The U.S. House of Representatives Committee on Science, Space and Technology Subcommittee on Oversight and the Subcommittee on Energy held a joint hearing titled Examining Vulnerabilities of America’s Power Supply on September 10, 2015. The purpose of the hearing was to “discuss various threats to the national electric grid, including: severe weather or other natural events; cyber, physical, or coordinated attacks; space weather; and electromagnetic pulse (EMP) attacks.”
From the Hearing Charter:
“As the electric grid continues to be modernized and become more interconnected, the threat of a potential cybersecurity breach significantly increases.”
“The concern with the two-way communication aspect of the ‘smart grid’ is that it opens up potential points of unauthorized system access and can present potential cybersecurity vulnerabilities. In addition, there are concerns with the security and privacy of smart electricity meters, which send data about energy use wirelessly to electric distribution companies and control the flow of power to customers.”
One of the expert witnesses was Nadya Bartol, Vice President, Industry Affairs and Cybersecurity Strategist for the Utilities Telecom Council (UTC). Hearing Chairman Loudermilk asked Ms. Bartol a question regarding smart meters. A video clip of this exchange is provided below followed by additional relevant information.
QUESTION FROM LOUDERMILK: I assume you are talking about a smart grid-type system. And part of that is the smart meters. Is there a vulnerability of having smart meters at home and what type of information are we gathering from that?
RESPONSE BY BARTOL: To my knowledge the information gathered from the smart meter is information about electricity usage. Nothing that qualifies as personal information is gathered.
RESPONSE BY BARTOL: The vulnerability lies in the fact that this is smart technology. This is IP Internet protocol accessible technology and lots of access points, a lot more access points than before. So the Swiss cheese is bigger, and you have more opportunity to come in. That’s the vulnerability.
Correction Provided by SkyVision Solutions: Possibly Ms. Bartol is a cybersecurity expert and not a privacy expert. Electricity usage information is “personal information” as noted below and as quoted from NISTIR 7628 Revision 1. The smart meter identifying number is also transmitted with the granular usage information which can then be associated with a specific customer account.
Personal Information as defined by NISTIR 7628 Revision 1, Guidelines for Smart Grid Cybersecurity, Volume 2 – Privacy and the Smart Grid, (September 2014); Appendix G, pages 174 and 175.
“Personal information is a broad term that includes personally identifiable information (PII) and addition to other types of information. Personal information may reveal information about, or describe, an individual, or group of individuals, such as a family, household, or residence. This information includes, but is not limited to, such information as name, Social Security number, physical description, home address, home telephone number, education, financial matters, medical or employment history, statements made by or attributed to the individual, and utility usage information, all of which could be used to impact privacy.”
“Personal information within the smart grid includes, but is not be limited to, information that reveals details, either explicitly or implicitly, about a specific individual’s or specific group’s type of premises and energy use activities. This is expanded beyond the normal ‘individual’ component because there could be negative privacy impacts for all individuals within one dwelling or building structure. This can include items such as energy use patterns, characteristics related to energy consumption through smart appliances, and other types of activities. The energy use pattern could be considered unique to a household or premises similar to how a fingerprint or DNA is unique to an individual.”
Supplemental Information Provided by SkyVision Solutions: One of the references listed in the Hearing Charter is a Congressional Research Service (CRS) document titled, “The Smart Grid and Cybersecurity — Regulatory Policy and Issues.” To supplement the testimony of Ms. Bartol, here is information quoted from the CRS document which provides additional insight as to why the “smart” wireless technology used by most smart meters is subject to unique cyber threat vulnerabilities:
“Grid devices capable of two-way communications are considered to be potential points of unauthorized system access, and can represent a potential cybersecurity vulnerability. While security protocols may exist to prevent unauthorized entry, wireless networks can be monitored and potentially hacked by cybercriminals. Smart meters are another example of new applications in which the security of data has been mentioned as a concern. At the heart of smart meters are semiconductor chips which allow data about energy use to be sent wirelessly to the electric distribution company, and which potentially allows the meter to control the flow of power to customers. The security of the encrypted information in the communications protocol used by many of these devices has been questioned in the past, and questions have been raised about the effectiveness of efforts to patch identified flaws. The primary consideration in the choice of wireless protocol by semiconductor providers seems to be cost of the system, a criteria which is not always compatible with cybersecurity goals for secure communications.”
“The components of smarter grid devices present another potential vulnerability concern. Most of the smart meter, sensor, and other equipment makers are international companies who obtain their components from international sources. Taiwan, Singapore, China, and South Korea are among the largest overseas manufacturers of semiconductors and microprocessors for smart devices. The reliable operation of semiconductor and microprocessor- based devices is based on the low-level firmware controlling the device’s basic functions. Firmware in the form of fixed machine- language binary code is found in almost all the electronic devices making up smarter grid products such as programmable controllers and programmable logic arrays. If a hacker or cybercriminal gained access to such devices (especially during the manufacturing process), a section of code could be covertly inserted in the device and activated in such a way as to impair its functioning in a reliable manner. Some might suggest random or statistically based testing of the firmware in smarter grid devices. But the impairment would not need to be placed in all such devices coming off an assembly line. If a large enough sample was impaired, the effect might be enough to cast doubt on the reliability of a whole class of such devices.”
Commentary and Analysis
Although it was gratifying to hear mention of smart meters at the September 10th Congressional hearing, it was disappointing that one of the expert witnesses apparently doesn’t realize that energy usage data is “personal information.” Thus the privacy invasion aspects of smart meters were inappropriately minimized or downplayed at the hearing.
On the subject of cyber threat vulnerability, the expert witness did reasonably describe the issue of lots and lots of access points with Internet accessible technology. The reference to “Swiss cheese” is appropriate to those understanding the phrase “more holes than Swiss cheese,” in that Ms. Bartol was likely referring to the fact that each smart meter could be thought of as an additional “hole” or possible point of entry into the grid system by hackers and others.
Overall, as with most Congressional hearings, there is not much hope for definitive action or follow-up. In any case, I wanted to publicize the smart meter exchange from the Congressional hearing that would otherwise likely get zero press coverage. For those interested in this topic and as a follow-up, please contact your legislative representatives and present them with your concerns and additional facts as outlined in this article.
Primary Source Material for this Article
Subcommittee on Oversight and Subcommittee on Energy Hearing – Examining Vulnerabilities of America’s Power Supply at https://science.house.gov/legislation/hearings/examining-vulnerabilities-america-s-power-supply-0