Search for content.
-
Featured Article on FCC: ‘Prime Example of Institutional Corruption’

Copyright Notice
© SkyVision Solutions and
Smart Grid Awareness
[https://smartgridawareness.org/], 2013 – 2025.Unauthorized use and/or duplication of material from this site without express and written permission from this site’s author and/or owner is strictly prohibited. Excerpts and links may be used, provided that full and clear credit is given to SkyVision Solutions and Smart Grid Awareness with appropriate and specific direction to the original content.
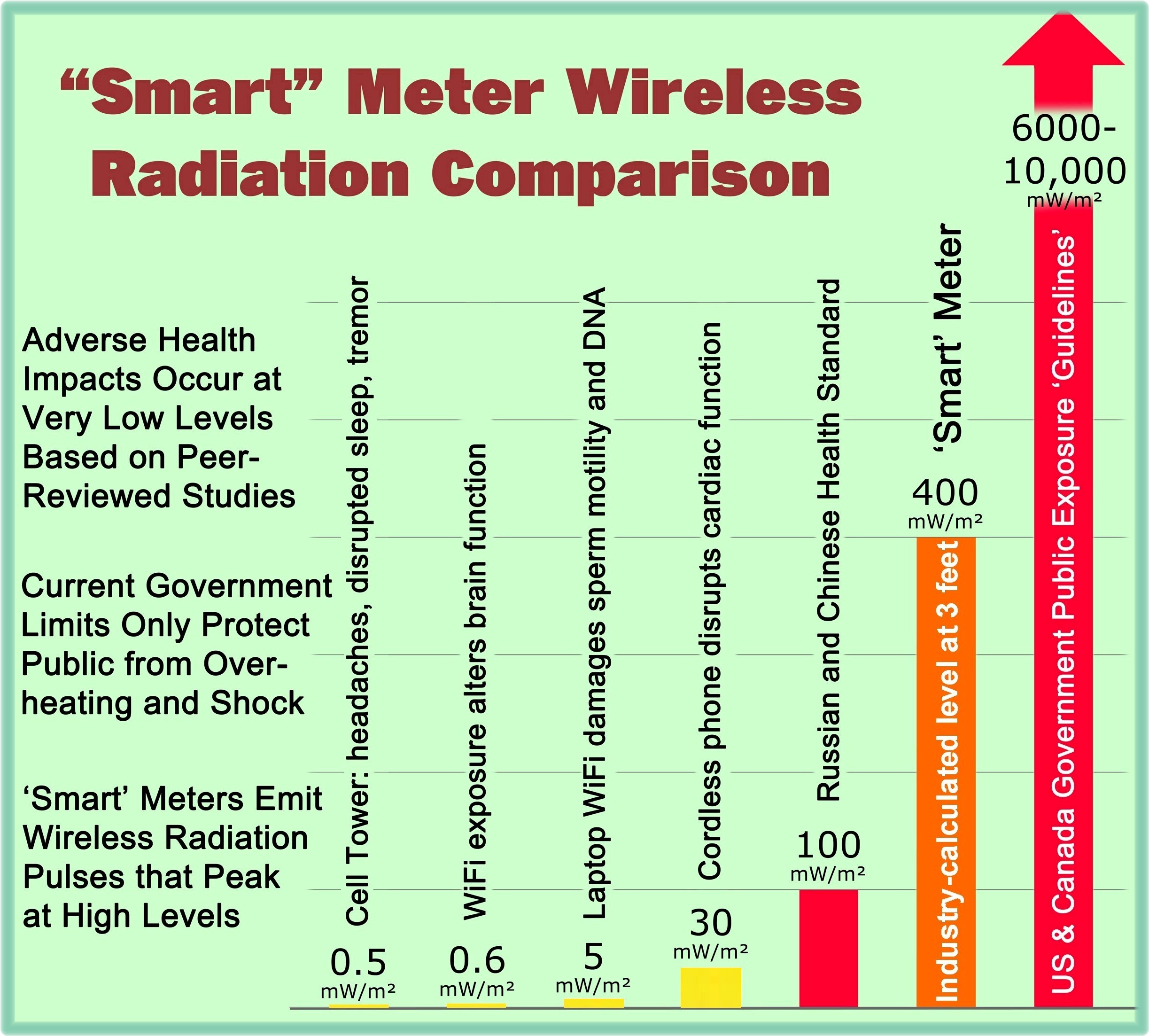
“Smart” Meter Wireless Radiation Comparison Chart
Smart Meter Remote Disconnect: An Unnecessary Cyber Risk
Archives

-
Helpful Links
-
- AAEM Call for Moratorium on Smart Meter Installations
- AAEM Medical Recommendations
- AAEM Position on Wireless RF in Schools
- AAEM Scientific Review of RF Fields Effect on Health
- American Academy of Pediatrics Letter on RF Exposure Limits
- BioInitiative Report
- CRS Report on Smart Meter Data: Privacy and Cybersecurity (2012)
- GAO Report for Telecommunication (2012)
- GAO Report on Smart Grid Cybersecurity (2011)
- Getting Smarter About the Smart Grid (2012)
- Health Impact Assessment (HIA) of the ComEd Smart Meter Deployment
- IARC Declaration for RF Fields as Possibly Carcinogenic (2011)
- NISTIR 7628, Revision 1, September 2014 (3 volumes)
- NISTIR 7628, Volume 2, Privacy, August 2010
- Procrustean Approach to Setting RF Exposure Standards
- Recommended External Link: Smart Meters, Fake News and the IoT
- Smart Metering & Privacy: Existing Law and Competing Policies (2009)
- Smart Meters: Correcting the Gross Misinformation
Video Clip: Dr. David McCormick Lecture Excerpt on Thermal vs. Nonthermal RF Effects
Daily Archives: November 21, 2015
From India: Smart Meter Cyber Attacks ‘Could Bring the Country Down to its Knees’
by K.T. Weaver, SkyVision Solutions The installation of ‘smart’ meters under India’s National Smart Grid Mission could pose a serious threat to the country’s critical infrastructure, one of India’s leading experts in cyber security has said. According to Sachin Burman, … Continue reading

